Who are we ...
Primary Area of Expertise:
- Offensive Cyber Security Strategies - "Assume Breach"
- Penetration Testing with Adversary Threat Simulation
- Active in the Cyber Security Community














Vulnerability Assessments (VA) − Independent expert review for a diverse set of potential vulnerabilities across a wide range of technologies.
Penetration Testing
Vulnerability Assessments
Vulnerability Research Exploit Development
Open Source Data Collection
Phishing
High Value Targets
Incident Response Testing
Incident Handling
Incident Response
Network Monitoring
Log Collection / Correlation
Threat Intelligence
End Point Protection
Automated Response
Policy / Consulting
Web Application Assessment
Software Assessment
Manual & Automated






Skillwerks is an on demand assessment platform to demonstrate individual computer skills and competencies.

Splunk− Delivering & Developing powerful operational intelligence by providing real-time insight into your information systems through dashboards, charts, reports, and alerts.

Vulnerability Assessments (VA) − Independent expert review for a diverse set of potential vulnerabilities across a wide range of technologies.
Assessment of adequacy and effectiveness of system security control measures
Evaluation of multiple technologies including:
Network & Operating Systems
Applications (Web & Thick Client)
Databases
Vulnerability
Threat
Asset

Penetration Testing (PT) − Implementation of proven testing methodology and lifecycle emulating modern threats
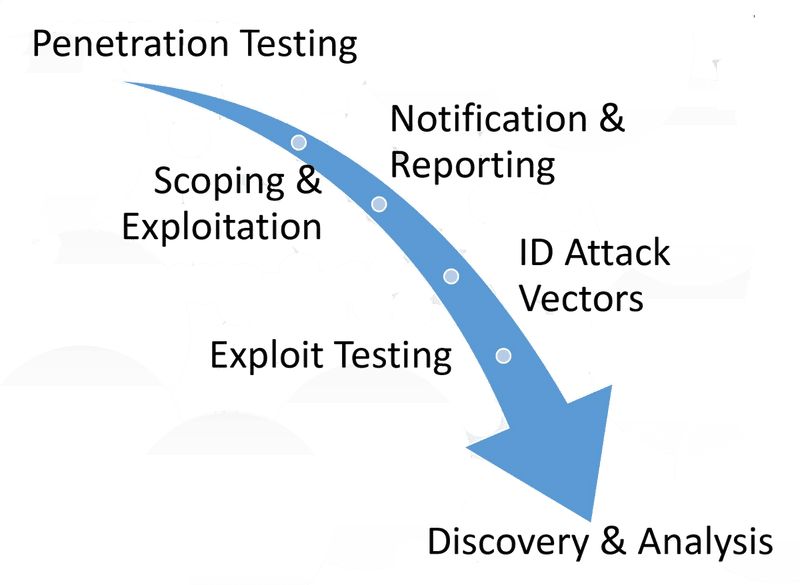
Assessment of security posture of 3rd party or custom developed applications across a wide range of operating platforms and attack perspectives.
Credited with over 15 CVEs for discovered vulnerabilities

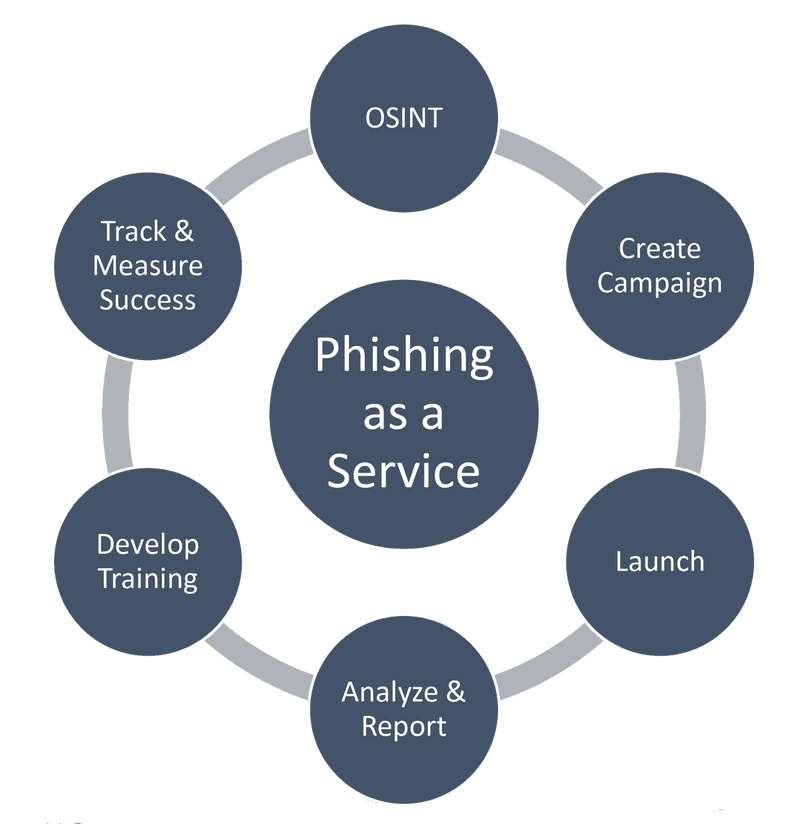
Impact analysis of a successfully executed social engineering campaign in a controlled environment
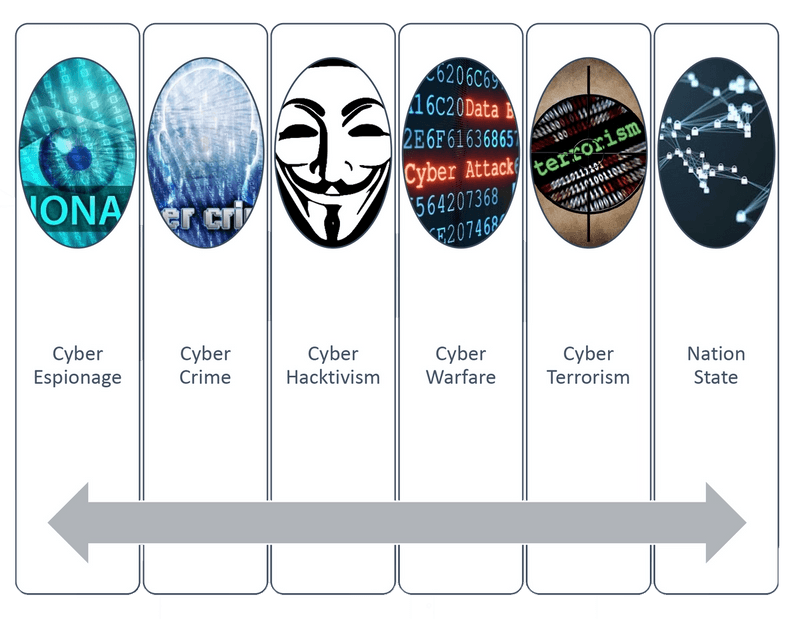
Emulation of advanced attack profiles (e.g., nation-state, highly funded criminal organization, Hacktivism)
Identifies potential ways an insider could threaten your organization

Gray Tier’s own developed variety of proactive services which evaluates an organization’s external security posture

